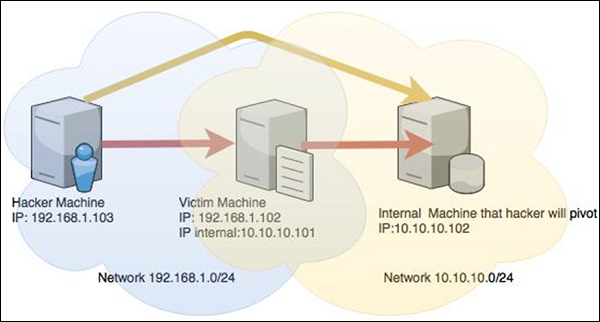
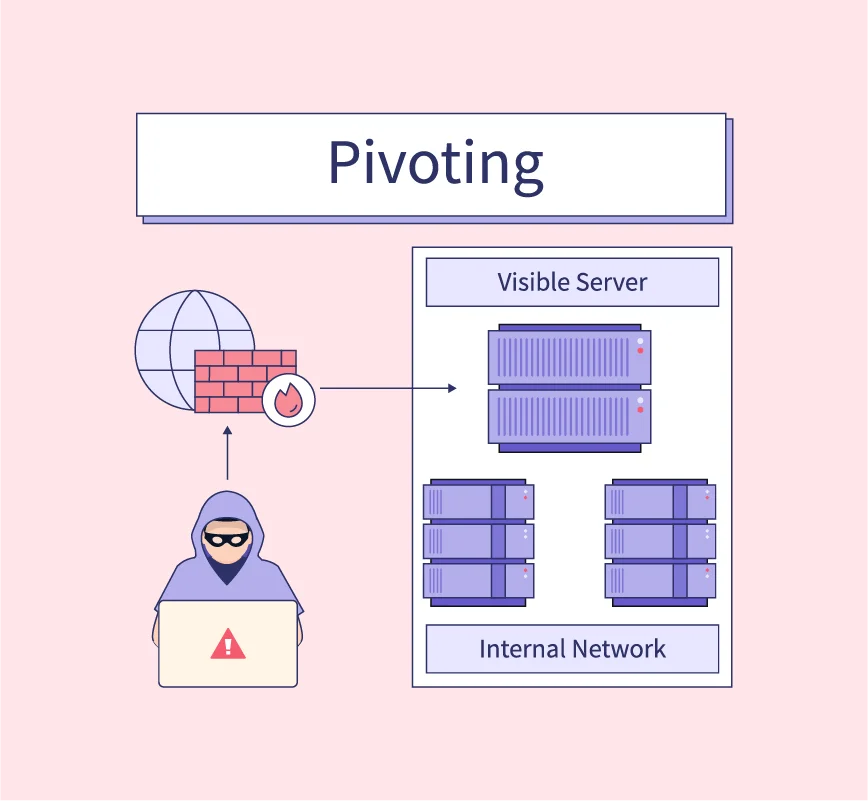
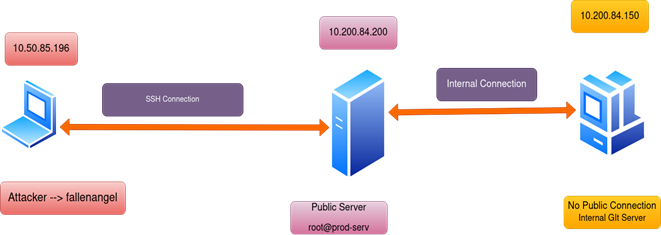
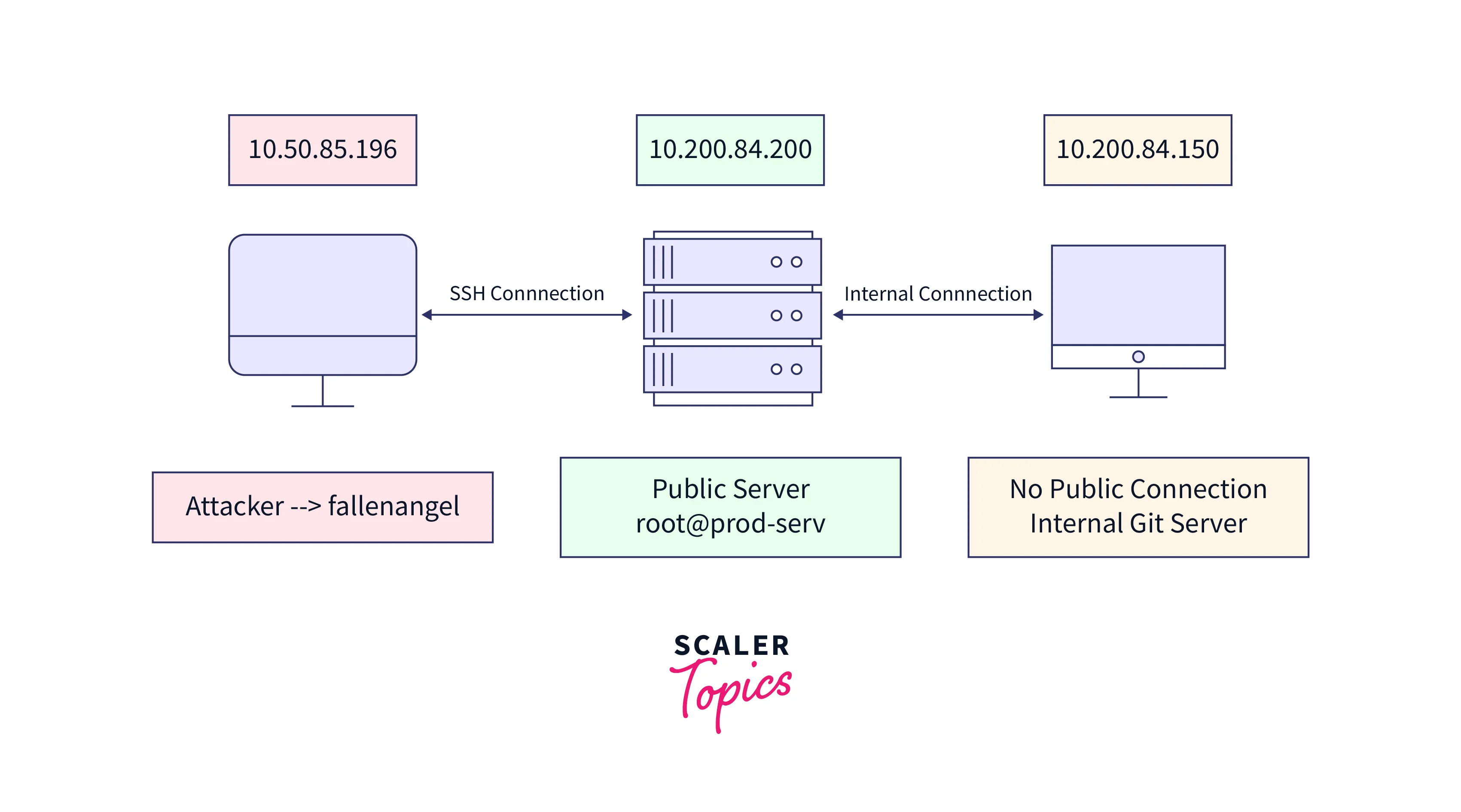
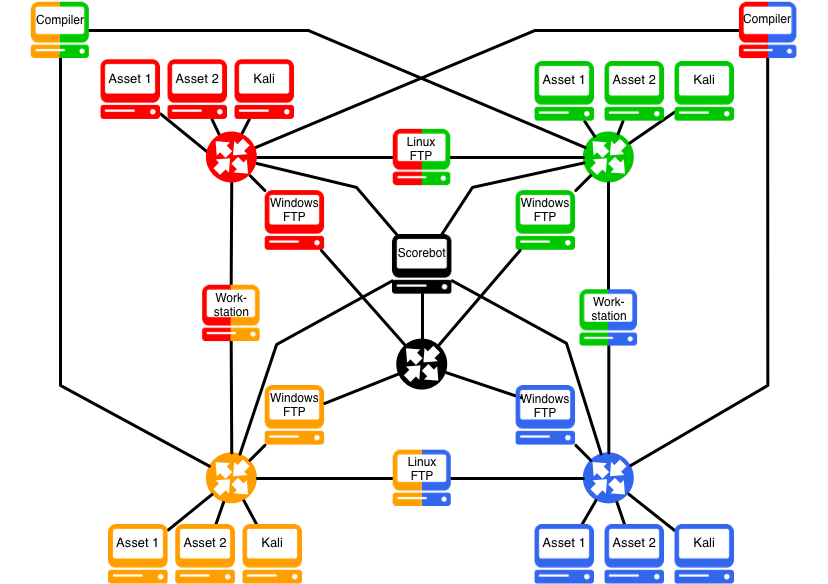
Web Security Geeks - The Security Blog: Metasploit Pivoting And Port Forwarding : Attacking Network - Pentesting Network

WiCyS Latina Affiliate | How to Pivot Into CyberSecurity Part 2- Career Changers | WiCyS - Women in Cybersecurity

Your Passport to a Cyber Security Career #1 | How Do We Pivot? | New Series | EP 27 by The Mega C-Suite Stories